5 Actionable Hacks to Master Key Account Feedback in Cybersecurity
In cybersecurity, your key accounts aren't just customers—they're strategic partners whose feedback can make or break your security posture. These organizations represent your most critical deployments, often handling sensitive data and complex threat landscapes that reveal vulnerabilities your internal testing might miss. Systematic feedback tracking transforms reactive security into proactive defense. When a financial institution reports a novel attack vector or a healthcare provider identifies compliance workflow issues, you're not just fixing a bug—you're strengthening your entire product ecosystem.
This continuous feedback loop enables rapid iteration on threat detection algorithms, authentication protocols, and incident response workflows. Practical tip: Create a 'critical feedback matrix' that categorizes input by threat level (critical/high/medium), affected security controls, and potential impact on other clients. This prioritization framework ensures you address the most pressing security concerns first while maintaining visibility into emerging patterns across your customer base.
The competitive advantage is undeniable. Companies that institutionalize key account feedback tracking consistently outperform competitors in industry evaluations. They're first to market with patches for emerging threats, build stronger customer loyalty through demonstrated responsiveness, and develop more robust security frameworks that become industry standards. In cybersecurity, the organization that listens best to its key accounts doesn't just win deals—it defines the future of digital defense.
Hack #1: Automate Feedback Collection with Integrated Monitoring Tools
Manual feedback collection is time-consuming and often misses critical insights from key accounts. By automating the process, you can capture real-time data and improve responsiveness to security needs. Stop manually chasing feedback by integrating monitoring tools directly into your security dashboards and portals.
Start by connecting your SIEM, EDR, or cloud security platforms via APIs to capture real-time usage patterns, alert response times, and system performance metrics. These data points reveal satisfaction levels before customers even voice concerns.
Practical Checklist: ✅
- Identify key security portals your accounts access daily.
- Integrate with platforms like Datadog, Splunk, or custom dashboards via REST APIs.
- Set up automated data collection for usage frequency, feature adoption, and error rates.
- Configure webhooks to trigger feedback surveys after specific security events (e.g., threat neutralization, compliance scans).
- Use automation tools to route low satisfaction scores directly to account managers for immediate follow-up.
Pro Tip: Trigger NPS surveys immediately after successful incident resolution. Customers are most engaged when they've just experienced your security solution's value. Capture feedback while the positive experience is fresh, then automatically route promoters to review platforms and detractors to your support team.
Hack #2: Create Structured Quarterly Security Review Sessions
Quarterly security reviews are essential for maintaining strong client relationships and ensuring your security measures are effective. Transform these sessions from routine check-ins into strategic feedback engines by designing standardized templates that capture consistent metrics across all key accounts.
Include sections for: threat landscape updates, incident response performance (MTTD/MTTR), security posture assessments, and client-specific concerns. This standardization ensures apples-to-apples comparisons and trend analysis over time.
Incorporate real-time threat intelligence into every review. Share relevant threat actor TTPs, emerging vulnerabilities affecting their industry, and benchmark their security maturity against peers. Use visual dashboards showing attack surface changes, security control effectiveness, and compliance status updates.
Most importantly, establish action-oriented follow-up processes. For each review finding, assign: (1) specific action items with owners, (2) clear deadlines, (3) success metrics, and (4) escalation paths for unresolved issues. Create a 30-60-90 day follow-up cadence to track progress. Pro tip: Use a RACI matrix to clarify responsibilities and maintain momentum between quarterly sessions.
Hack #3: Leverage Competitor Intelligence for Comparative Feedback Analysis
Understanding how your solution compares to competitors is crucial for strategic planning in cybersecurity. When key accounts provide feedback, it's not just about your solution—it's about how you stack up against the competition. Use competitor intelligence to transform isolated comments into actionable insights.
Practical Steps:
- Map Feedback to Competitor Offerings: When clients mention "feature X is slow," check if competitors highlight speed as a strength. Automated tools can track competitor messaging and customer reviews efficiently.
- Identify Capability Gaps: If multiple accounts praise a competitor's 24/7 SOC support, that's a gap to address. Create a matrix comparing feedback on security, support, and pricing across key rivals.
- Benchmark Against Industry Standards: Use competitor performance as a baseline. For example, if industry leaders boast 99.9% uptime in case studies, measure your feedback against that standard.
Quick Checklist: ✅
- Monitor competitor review sites (e.g., G2, Capterra) for trending complaints.
- Track competitor case studies for featured capabilities.
- Analyze win/loss reports for direct comparisons.
- Set up alerts for competitor pricing or feature changes.
Tip: Don't just react to feedback—proactively ask accounts: "How does our threat detection compare to Vendor Y's solution you evaluated?" This positions you as strategically aware while gathering competitive intelligence.
Example: Tracking Competitor Events
Trackunit will attend CONEXPO-CON/AGG 2026 in March at Booth N12707 in Las Vegas.
Why it matters: Monitoring competitor participation in industry events helps you understand their market presence, networking strategies, and potential product launches. This insight allows you to anticipate competitive moves and align your feedback analysis with industry trends.
Hack #4: Implement Real-Time Feedback Channels for Incident Response
Immediate communication during crises is vital for trust and efficiency in cybersecurity. Real-time feedback channels ensure that all stakeholders are aligned and informed, reducing response times and improving outcomes. During security incidents, establish dedicated communication channels between your SOC team and key account stakeholders.
Use secure collaboration platforms like Slack channels or Microsoft Teams groups specifically for incident updates. Create a tiered communication structure: technical updates for SOC analysts, operational summaries for account managers, and executive briefings for leadership.
Practical Checklist: ✅
- Set up encrypted incident communication channels accessible to both SOC teams and key account contacts.
- Implement a "single source of truth" dashboard showing real-time incident status.
- Create pre-approved message templates for different incident severity levels.
- Schedule immediate post-incident debriefs within 24 hours of resolution.
- Document all decisions and communications for traceability and future improvement.
Post-Incident Analysis: After each incident, conduct structured after-action reviews (AARs) with both technical teams and account stakeholders. Use these sessions to gather actionable improvement suggestions focusing on communication effectiveness, response coordination, and stakeholder satisfaction. Create feedback loops by implementing the top 3 improvement suggestions within 30 days and reporting back to stakeholders on changes made.
Key Tip: Establish regular quarterly tabletop exercises involving both SOC teams and key account representatives to practice incident communication protocols and refine feedback mechanisms before real crises occur.
Hack #5: Build a Centralized Feedback Dashboard with Actionable Insights
A fragmented approach to feedback management leads to missed opportunities and delayed responses in cybersecurity. Centralizing all feedback into a single dashboard provides clarity and enables proactive action to enhance security postures. Stop juggling feedback from disparate sources like support tickets, NPS surveys, and customer calls.
Consolidate everything using tools that track competitor mentions, customer sentiment, and account health scores in one place. This gives you a holistic view of each key account's satisfaction and potential risks.
Set up automated alerts for negative feedback triggers—like a sudden drop in CSAT scores or mentions of competitor solutions in your accounts. Configure thresholds (e.g., alert if satisfaction falls below 80%) so your team can intervene proactively before churn risks escalate.
Transform raw data into strategic decisions with executive dashboards. Use visualizations to highlight trends: Are certain features causing frustration? Is a competitor gaining traction? Include actionable insights, such as "Prioritize feature X based on 30% negative feedback" or "Launch retention campaign for accounts with declining scores."
Practical Steps:
- Integrate data sources (CRM, surveys, social media).
- Define key metrics (e.g., sentiment score, churn risk).
- Automate alerts for real-time monitoring.
- Schedule weekly reviews to adjust strategies based on insights.
Example: Tracking Partnerships
Rakuten Card Linked Offer Network announced a new card-linked rewards partnership with OnePay, expanding how rewards are delivered within financial platforms.
Why it matters: Monitoring competitor partnerships reveals business expansions, new market entries, and collaborative strengths. This helps you assess competitive threats and refine your feedback strategies to address evolving market dynamics.
Conclusion: Turning Feedback into Competitive Advantage
Transform key account feedback into sustainable competitive advantage by implementing a continuous improvement cycle. Weekly feedback review sessions with security and product teams ensure timely actions, while quarterly competitive positioning analysis using feedback patterns keeps you ahead of rivals.
Continuous Improvement Cycle:
- Weekly feedback review sessions with security and product teams.
- Quarterly competitive positioning analysis using feedback patterns.
- Create feedback-to-feature mapping matrix to prioritize development based on client needs.
ROI Measurement Framework:
- Track retention rate improvements among feedback-engaged accounts.
- Measure expansion revenue from accounts where feedback was implemented.
- Calculate competitive win rates against monitored competitors post-feedback.
- Use dashboard KPIs: feedback implementation rate, security partnership growth, threat detection improvements.
Security Partnership Building:
- Establish transparent feedback sharing protocols with key accounts.
- Create joint security review committees with top 5% of accounts.
- Implement feedback acknowledgment system with clear timelines.
- Develop co-innovation opportunities based on shared security challenges.
Actionable Checklist: ✅
✅ Document all feedback with source, date, and priority level.
✅ Assign ownership for each feedback item to specific team members.
✅ Set implementation timelines and communicate progress to accounts.
✅ Measure impact through quarterly security posture assessments.
✅ Share anonymized insights across your customer base to demonstrate value.
Example: Tracking Management Changes
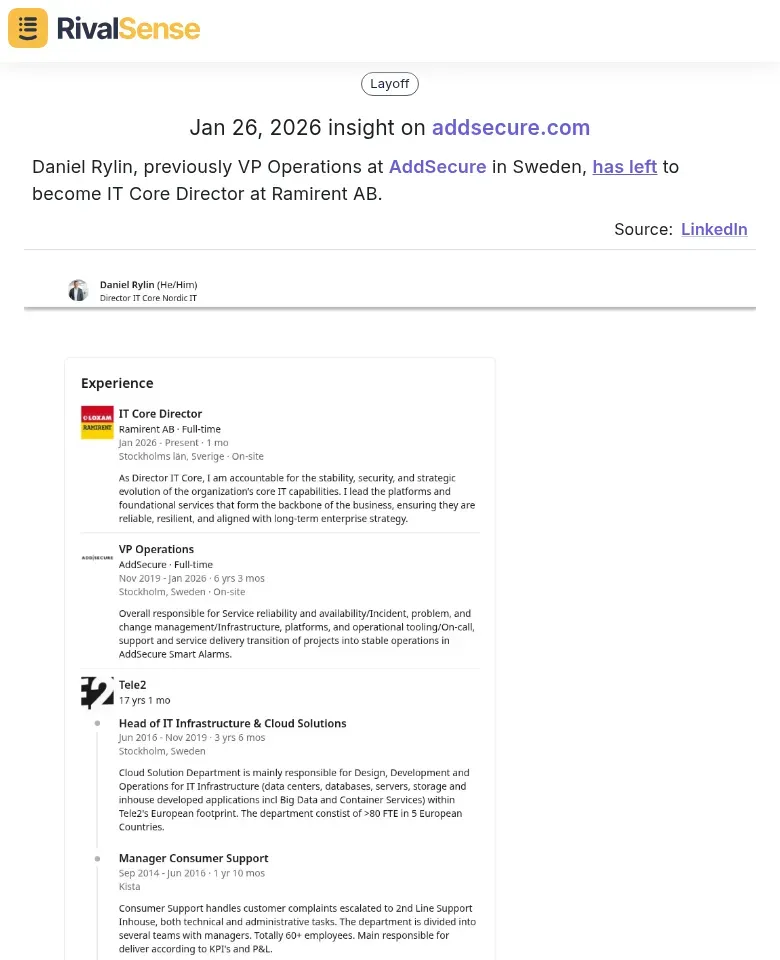
Daniel Rylin, previously VP Operations at AddSecure in Sweden, has left to become IT Core Director at Ramirent AB.
Why it matters: Management changes can signal strategic shifts, new initiatives, or talent acquisitions in competitors. By monitoring such moves, you can anticipate changes in their product focus or market approach, allowing you to adjust your feedback analysis and stay competitive.
Pro tip: Integrate feedback tracking with your competitive intelligence platform to correlate customer insights with competitor moves, creating a powerful feedback loop that drives both customer satisfaction and market leadership.
To effectively implement these hacks and stay ahead of competitors, try RivalSense for free at https://rivalsense.co/. Get your first competitor report today and start transforming feedback into strategic insights for your cybersecurity business.
📚 Read more
👉 From Monitoring to Action: How Real-Time Competitor Intelligence Drives Strategic Wins
👉 From Tracking to Winning: How Competitor Insights Unlock Key Account Opportunities
👉 Predictive Analytics for Key Account Monitoring: A Web Scraping Guide for B2B Leaders
👉 Data-Driven Insights: How Competitor Partnerships & Client Wins Reveal Hiring Strategies
👉 How to Leverage Competitor Executive Changes for Strategic Insights
