Dark Web Intelligence: Strategic Competitive Differentiation in Cybersecurity
In the rapidly evolving cybersecurity landscape, dark web intelligence has emerged as a critical tool for businesses seeking competitive differentiation. This intelligence involves monitoring and analyzing activities on the dark web to uncover potential threats, vulnerabilities, and emerging trends before they surface on the public internet. By leveraging this data, organizations can proactively address risks and stay ahead of adversaries.
The growing importance of competitive differentiation in cybersecurity cannot be overstated. With cyber threats becoming more sophisticated, businesses must adopt advanced strategies to protect their assets and maintain trust. Dark web intelligence provides a strategic advantage by offering insights into hacker forums, leaked credentials, and underground marketplaces, enabling companies to anticipate and mitigate attacks.
✅ Practical Steps to Harness Dark Web Intelligence:
- Identify Key Threats: Focus on monitoring dark web channels relevant to your industry.
- Invest in Tools: Utilize specialized software to automate monitoring.
- Collaborate with Experts: Partner with cybersecurity firms for deeper analysis.
- Act on Intelligence: Develop response plans based on gathered insights.
- Stay Updated: Continuously refine your approach as new threats emerge.
📚 Leveraging Content Strategy for Competitive Edge
In the cybersecurity arena, a diversified content strategy is essential for differentiation. Tracking competitors' content evolution reveals market trends and audience engagement tactics, helping you refine your own approach. For instance, monitoring resource section updates can signal strategic shifts in educational positioning.
Consider how Searchlight Cyber recently revamped their resources section: replacing 'Whitepapers & Reports' with dedicated 'eBooks' and 'Whitepapers' categories while adding timely content like 'DARK WEB DRUG MARKET TAKEDOWN' and 'CARTIER DATA BREACH ANALYSIS'.
This insight is valuable because it reveals how competitors adapt content to emerging threats—enabling you to benchmark your strategy and identify content gaps.
🛠️ Actionable Framework:
- Audit content quarterly using competitor insights
- Repurpose top-performing pieces into new formats (e.g., webinar → ebook)
- Align topics with recent incidents (e.g., dark web takedowns)
💡 Innovative Techniques in Cybersecurity
Staying ahead requires mastering emerging attack vectors like Server-Side Request Forgery (SSRF). These techniques expose critical vulnerabilities before exploitation, offering opportunities for preemptive solutions. Real-time tracking of technical innovations positions your offerings at the forefront.
RivalSense detected Searchlight Cyber's breakthrough: a novel SSRF technique using HTTP redirect loops to leak full HTTP responses.
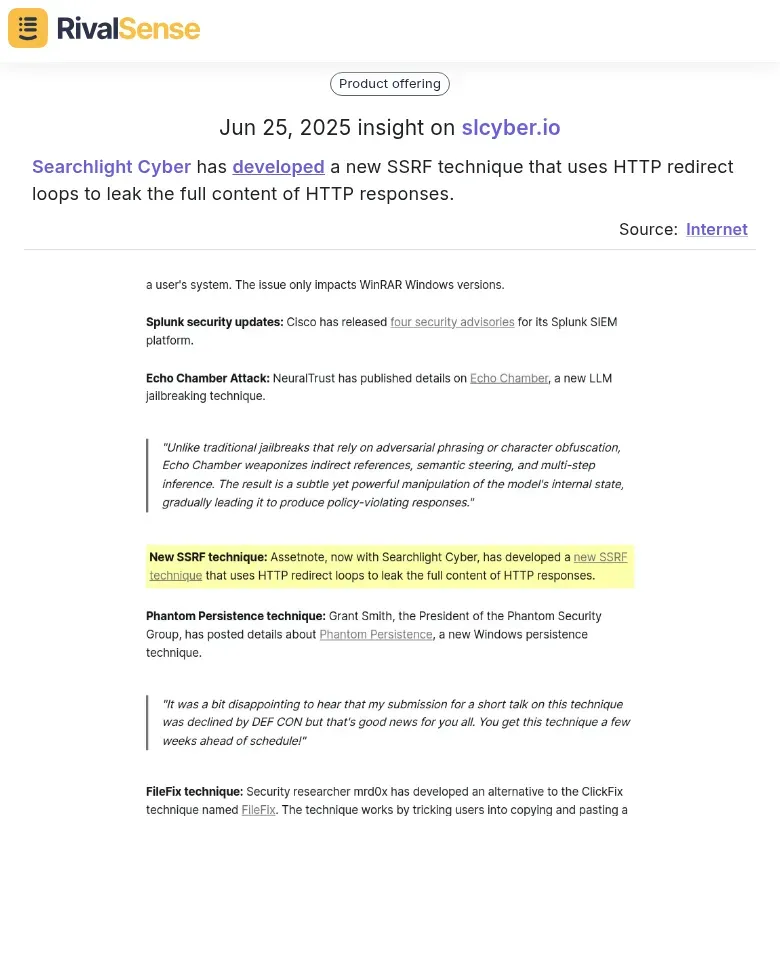
Monitoring such developments is crucial—it informs your R&D priorities and helps develop countermeasures faster than competitors.
🔧 Implementation Checklist:
- Test external endpoints for SSRF vulnerabilities
- Analyze redirect chains for insecure patterns
- Update WAF rules based on latest attack methods
- Document findings in threat intelligence repositories
🤝 Collaborations and High-Impact Operations
Partnerships with agencies like the U.S. Department of Justice amplify threat disruption capabilities while boosting brand credibility. These collaborations signal market leadership and often precede client acquisition opportunities. Tracking them reveals partnership blueprints worth emulating.
Example: RivalSense observed Searchlight Cyber supporting the BidenCash dark web marketplace takedown—impacting 117k+ users and $17M+ in illicit transactions.
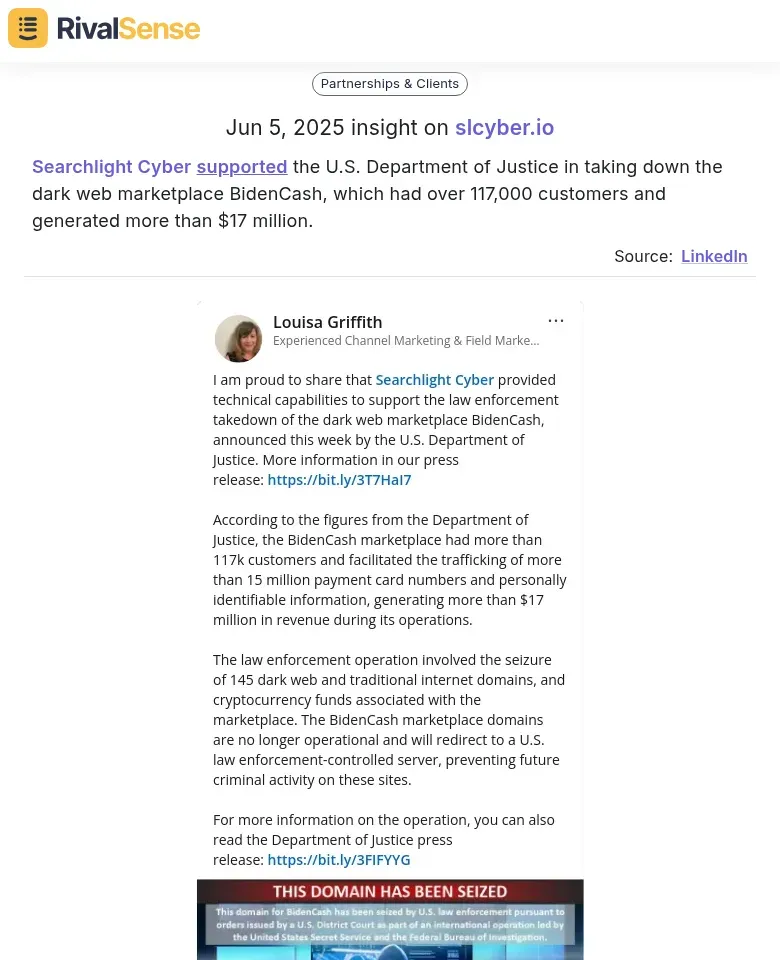
Such insights demonstrate how operational visibility can inspire similar initiatives while positioning your firm as an industry authority.
🚀 Strategic Playbook:
| Step | Action |
|---|---|
| 1 | Identify agencies aligned with your security focus |
| 2 | Develop mutual-value partnership proposals |
| 3 | Measure/report operational impact metrics |
| 4 | Showcase successes through case studies |
🛡️ Building a Robust Cybersecurity Framework
Integrating dark web intelligence into security frameworks transforms reactive defense into proactive threat hunting. This requires continuous adaptation as underground tactics evolve. The most resilient organizations treat intelligence as a living system, not a static component.
Key integration pillars include:
- Automated threat feeds synced with SIEM systems
- Cross-functional response protocols for intelligence activation
- Quarterly TTP (Tactics, Techniques, Procedures) mapping against industry threats
📌 Critical Implementation Steps:
- Prioritize threats targeting your sector (e.g., financial, healthcare)
- Validate dark web monitoring tools against false-positive rates
- Conduct war-gaming exercises using latest dark web intelligence
🔮 Conclusion and Future Outlook
Dark web intelligence delivers unmatched competitive differentiation by revealing hidden threats, competitor innovations, and partnership opportunities. As cyber threats grow more sophisticated, differentiation will increasingly hinge on predictive capabilities fueled by AI-driven dark web analytics and cross-industry intelligence sharing.
Sustained Advantage Checklist:
- Monitor dark web forums for brand/industry mentions
- Invest in ML tools for threat pattern prediction
- Establish formal intelligence-sharing consortiums
- Conduct bi-monthly security protocol stress tests
Ready to Decode Competitor Strategies?
Automate your competitive intelligence with RivalSense. Track product launches, pricing changes, partnerships, and dark web activities—delivered in weekly actionable reports.
👉 Get your first competitor report today!
📚 Read more
👉 Unlock Growth: Actionable Competitor Pricing Insights & Frameworks 🚀
👉 Analyzing Smartling's Leadership Expansion: Strategic Implications for Competitors
👉 Beyond Data Overload: Building a Market Intelligence Framework That Predicts Shifts
