Cybersecurity Key Account Identification: 2025 Trend Analysis
In 2025, cybersecurity key account identification has become a cornerstone of strategic growth for B2B companies. This process focuses on pinpointing high-value clients—such as enterprises in finance, healthcare, or critical infrastructure—that drive significant revenue and foster long-term partnerships. Its importance has surged due to escalating cyber threats, regulatory pressures, and rapid digital transformation, making precise targeting essential for optimizing resources and differentiating in crowded markets. Key trends this year include the rise of AI-driven threat intelligence, zero-trust architectures, and stricter compliance demands (e.g., GDPR updates), all reshaping how accounts are prioritized. By concentrating on key accounts, businesses can achieve enhanced customer retention, higher ROI from tailored solutions, and greater competitive agility.
Practical Steps to Get Started:
- ✅ Analyze industry reports and competitor client lists to identify lucrative sectors.
- ✅ Use data analytics to assess account potential based on budget, threat exposure, and past incidents.
- ✅ Develop personalized outreach strategies, such as offering compliance audits or AI-based security assessments.
💡 Tip: Regularly update your account criteria to adapt to evolving threats and market shifts for sustained relevance.
Emerging Technologies Shaping Key Account Strategies
Artificial intelligence and machine learning are fundamentally changing how key accounts are identified in cybersecurity. These technologies analyze vast datasets to uncover high-value prospects by processing threat intelligence, compliance needs, and historical incident data. For instance, ML algorithms can score accounts based on risk exposure and budget allocation, enabling more informed prioritization. Additionally, zero-trust architectures are shifting focus toward organizations with mature security postures, as this model requires continuous verification and micro-segmentation.
Tracking competitor investments in emerging tech can provide early signals of market shifts. For example, RivalSense identified that Guardian is hiring for a Head of Engineering – Intelligent Automation position in the United States to lead the development of automation solutions and intelligent self-service technologies.  This type of insight is valuable because it reveals where competitors are bolstering capabilities, helping you anticipate trends and refine your account strategies proactively.
This type of insight is valuable because it reveals where competitors are bolstering capabilities, helping you anticipate trends and refine your account strategies proactively.
Checklist for Evaluating Prospects:
- 🔍 Assess adoption of multi-factor authentication and network segmentation policies.
- 📊 Use AI tools to analyze account attributes like industry sector, company size, and recent breaches.
- 🎯 Prioritize accounts with continuous monitoring capabilities and readiness for zero-trust models.
Steps for Implementation:
- Integrate AI-powered platforms that automate data collection from diverse sources.
- Apply predictive analytics to forecast account potential based on growth trajectory and tech stack complexity.
- Allocate resources to targets with the highest conversion probability to drive revenue growth efficiently.
Competitive Intelligence in Cybersecurity Account Targeting
In 2025, competitive intelligence is revolutionizing how cybersecurity firms target key accounts by providing real-time insights into rival movements. By analyzing competitor client portfolios, you can identify underserved enterprise accounts—those using outdated solutions or facing emerging threats—and capitalize on gaps in the market. For example, if a competitor focuses heavily on financial services, sectors like healthcare or manufacturing may present untapped opportunities. Monitoring competitor announcements through press releases, case studies, and social media allows for agile adjustments to your targeting strategies.
Management changes at competitors can signal strategic shifts that impact account targeting. RivalSense tracked that Michael Rozsa joined New York Life as Corporate Vice President and Actuary in the United States, previously serving as Principal at Gallagher.  This type of insight is valuable because it highlights leadership transitions that may indicate new focuses on risk management or actuarial innovations, enabling you to align your outreach with evolving competitor priorities.
This type of insight is valuable because it highlights leadership transitions that may indicate new focuses on risk management or actuarial innovations, enabling you to align your outreach with evolving competitor priorities.
Practical Steps to Leverage Competitive Intelligence:
- 🗺️ Map competitor key accounts by industry and size to identify coverage gaps.
- ⚠️ Set up alerts for competitor announcements on product launches, pricing changes, and partnerships.
- 🎯 Analyze gaps in competitor offerings—e.g., lack of AI-driven threat detection for mid-market firms—and tailor solutions to fill them.
💡 Tip: Use tools like RivalSense to track competitor feature launches and customer reviews, ensuring you pivot quickly to secure high-value accounts before rivals react.
Data-Driven Approaches for Account Identification and Segmentation
Data-driven approaches are essential for precise account identification and segmentation in 2025, leveraging multiple sources to build comprehensive profiles. By aggregating data from CRM systems, market intelligence platforms, and threat intelligence feeds, businesses can create 360-degree views of potential accounts. This involves analyzing firmographic data—such as industry, company size, revenue, and location—alongside behavioral indicators like recent security incidents or technology adoption patterns to score and prioritize targets effectively.
Segmentation allows for tailored outreach by categorizing accounts into groups like industry verticals (e.g., finance, healthcare), organizational sizes (SMBs vs. enterprises), and threat exposure levels (e.g., high-risk sectors prone to ransomware). Integrating internal CRM data with external insights ensures that pain points, such as compliance gaps or past breaches, are highlighted for personalized engagement. This method maximizes ROI by focusing efforts on accounts most likely to convert and retain.
Practical Steps for Implementation:
- 🔄 Set up automated data pipelines from sources like LinkedIn Sales Navigator and cybersecurity reports.
- 🧩 Apply clustering algorithms to group accounts with similar risk profiles and needs.
- 📈 Use scoring models to prioritize high-value targets based on factors like budget and threat landscape.
💡 Tip: Regularly update your data sources to reflect market shifts and employ predictive analytics to forecast emerging threats, keeping your strategies agile and responsive.
Challenges and Best Practices in 2025 Cybersecurity Account Management
Cybersecurity account managers in 2025 face significant hurdles in identifying and engaging key accounts, driven by complex enterprise needs and rapidly evolving threat landscapes. Distinguishing high-value clients from general leads becomes challenging amid regulatory changes like the EU's NIS2 Directive and evolving GDPR requirements, which add compliance pressures and demand constant adaptation. Additionally, the sheer volume of data and the need for real-time responses can overwhelm teams, making it crucial to implement structured approaches for sustained success.
To overcome these obstacles, adopt best practices that emphasize data-driven identification and proactive relationship management. For account identification, use scoring models that weigh factors such as company size, industry risk profile, past security incidents, and cybersecurity budget allocations. For relationship maintenance, schedule regular check-ins—such as quarterly business reviews—and provide proactive threat intelligence updates to demonstrate ongoing value and build trust through transparency.
Checklist for Onboarding Key Accounts:
- ✅ Verify compliance status and assess security maturity during initial evaluations.
- ✅ Set clear communication channels and expectations for incident response.
- ✅ Conduct annual audits to align security protocols with new regulations and update client contracts accordingly.
Best Practices Summary:
- Account Identification: Leverage AI tools to analyze data and score accounts objectively.
- Relationship Maintenance: Foster trust with regular updates and transparent handling of issues like data breaches.
- Regulatory Adaptation: Use regulatory tracking software to stay updated and adjust strategies dynamically.
💡 Tip: Create a feedback loop where insights from client interactions inform your account scoring models, ensuring continuous improvement in your targeting efforts.
Future Outlook and Strategic Recommendations
Looking beyond 2025, key account identification in cybersecurity will evolve from static lists to dynamic, AI-driven ecosystems that respond in real-time to threats and opportunities. Predictive analytics will play a central role in flagging emerging risks and customer vulnerabilities, with tools like RivalSense enabling continuous monitoring of competitor moves, market shifts, and regulatory changes. This shift demands a proactive approach, where businesses integrate advanced methodologies to stay ahead of the curve and turn uncertainty into sustained growth.
Strategic recommendations include adopting AI-powered platforms for automated data collection from diverse sources like the dark web and social media, and using machine learning to analyze patterns for account prioritization. For instance, a financial firm might focus on clients in regions with rising cyberattacks based on predictive insights. Additionally, leadership changes can indicate strategic pivots; RivalSense tracked that Nolan Melton Bennett, ALMI joined New York Life as Corporate Vice President, Director of AI Solutions and Business Insights in the United States, previously serving at Prudential Financial. 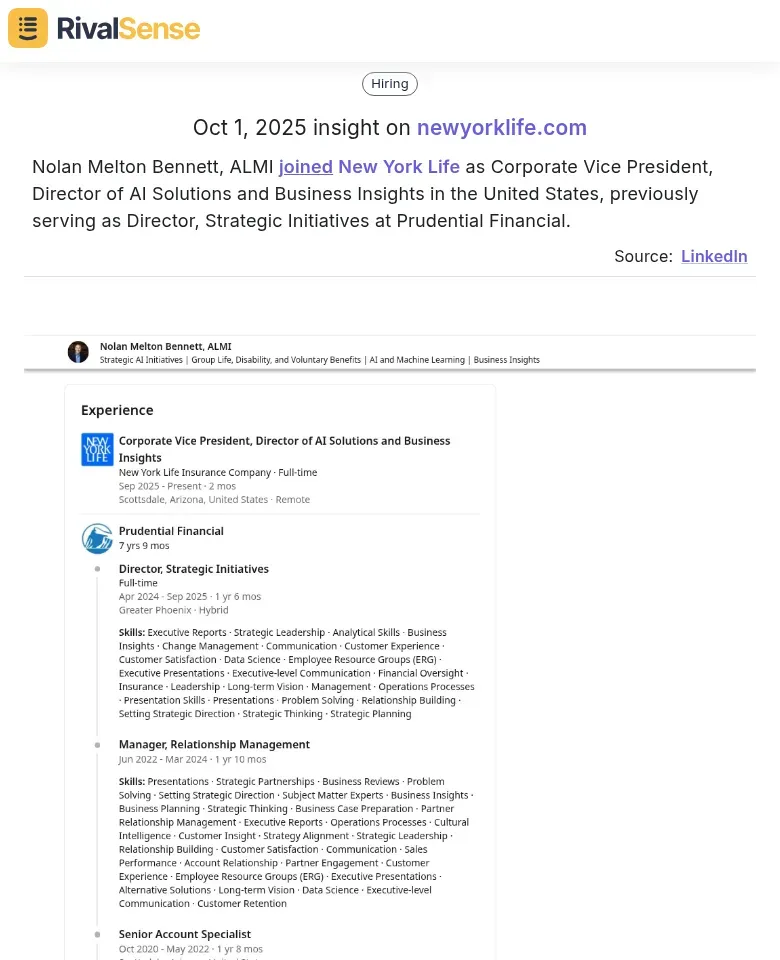 This type of insight is valuable because it reveals competitor investments in AI and data-driven solutions, allowing you to anticipate their direction and adjust your account strategies to capitalize on emerging trends.
This type of insight is valuable because it reveals competitor investments in AI and data-driven solutions, allowing you to anticipate their direction and adjust your account strategies to capitalize on emerging trends.
Steps to Build a Resilient Strategy:
- 🔍 Audit current tools and processes quarterly to ensure they align with future trends.
- 🔁 Implement a feedback loop where insights from competitor trackers inform account scoring and outreach.
- 🤝 Foster partnerships for shared intelligence and cross-train teams in threat analysis and competitive analysis.
💡 Tip: Start with pilot accounts to test new AI-driven approaches, scaling up as data validates outcomes for minimal risk and maximum impact.
🚀 Ready to enhance your cybersecurity account strategy? Try out RivalSense for free at https://rivalsense.co/ and get your first competitor report today! RivalSense tracks competitor product launches, pricing updates, event participations, partnerships, and more, delivering all insights in a weekly email report to keep you ahead of the competition.
📚 Read more
👉 How RivalSense Alerted Competitors to Civinity's Service Shift
👉 Quick Facebook Hacks for Competitor Branding Insights
👉 FinTech Competitor Journey Mapping: A Strategic Benchmarking Guide
👉 Master Competitor Event Tracking: Practical Insights for B2B Leaders
