Cybersecurity Competitive Intelligence: Key Account Tracking Software Comparison
Introduction: Why Cybersecurity Demands Advanced Competitive Intelligence
In today's rapidly evolving cybersecurity landscape, where new threats emerge daily and market dynamics shift overnight, traditional competitor monitoring is no longer sufficient. The stakes are too high for reactive approaches. Cybersecurity demands advanced competitive intelligence that transforms raw data into actionable strategic insights.
Practical Checklist for Cybersecurity Competitive Intelligence:
- Monitor key accounts daily - Track competitor wins, partnerships, and technology adoption patterns
- Analyze threat intelligence feeds - Correlate competitor moves with emerging attack vectors
- Map technology stacks - Understand which solutions your competitors are integrating
- Track executive movements - Leadership changes often signal strategic shifts
- Monitor regulatory compliance updates - Anticipate how competitors will adapt to new requirements
Key account tracking software becomes your strategic advantage by automating these processes. Instead of manual research, you get real-time alerts when competitors win major deals, launch new features, or form strategic partnerships. This enables you to anticipate market shifts before they happen and position your solutions accordingly.
For cybersecurity partnerships and technology adoption decisions, competitive intelligence provides critical context. When evaluating potential partners or considering new technology integrations, understanding how competitors are approaching similar decisions can reveal market trends and validate your strategic direction. The right intelligence platform transforms scattered data points into a coherent competitive narrative that informs every business decision.
Core Capabilities: What to Look for in Key Account Tracking Software
Selecting the right key account tracking software is crucial for effective cybersecurity competitive intelligence. You need tools that deliver precise, timely insights to stay ahead. When evaluating options, focus on three core capabilities that deliver actionable insights.
First, real-time monitoring of competitor partnerships and strategic alliances. Look for software that automatically tracks joint announcements, co-marketing initiatives, and technology integrations between competitors and their partners. Practical tip: Set up alerts for competitor mentions alongside major cloud providers (AWS, Azure, Google Cloud) and security technology partners to detect emerging alliances before they impact your market position.
Second, comprehensive tracking of industry event participation and thought leadership positioning. The best platforms map competitor speaking engagements, booth presence, and sponsorship levels across major cybersecurity conferences (RSA, Black Hat, DEF CON). Checklist item: Ensure the software tracks not just event attendance but also analyzes presentation themes to identify strategic focus areas and messaging shifts.
Third, automated detection of technology integrations and solution deployments. Advanced systems use AI to monitor competitor case studies, customer testimonials, and implementation announcements. Key feature to verify: The software should categorize deployments by industry vertical (finance, healthcare, government) and solution type (endpoint protection, cloud security, identity management) to reveal market penetration patterns.
Pro tip: Prioritize platforms offering customizable dashboards that combine these three data streams, enabling you to correlate partnership announcements with event presence and customer deployments for complete competitive intelligence.
Strategic Partnership Intelligence: Learning from Cybersecurity Alliances
Strategic partnerships are the lifeblood of cybersecurity innovation, transforming competitive threats into revenue opportunities. To identify revenue-generating alliances, track joint go-to-market announcements, co-branded webinars, and integrated product launches. Look for partnerships with clear ROI metrics like joint customer wins, revenue-sharing agreements, or bundled pricing models.
For example, RivalSense tracked how HUMAN and TollBit partnered in January 2025 to stop unauthorized AI content scraping agents and transform bot traffic into recurring revenue, according to TollBit CEO Toshit Panigrahi. This type of insight is valuable because it reveals how competitors are leveraging partnerships to address emerging threats and create new revenue streams, helping you assess similar opportunities for your business.

Analyze technology integration patterns by monitoring API documentation updates, SDK releases, and integration roadmaps. When competitors announce deep integrations (like SIEM-to-EDR connections), it often signals market consolidation trends. Create a partnership matrix tracking integration depth, technology stack compatibility, and customer adoption rates.
Monitor cross-industry collaborations that expand solution ecosystems. Cybersecurity firms partnering with cloud providers, MSPs, or industry-specific platforms create defensible market positions. Track these alliances through:
- Joint press releases and case studies
- Shared booth presence at major conferences
- Co-authored whitepapers and research
- Cross-referenced customer testimonials
Practical tip: Set up alerts for partnership announcements from key competitors, then analyze the partnership's strategic fit, revenue potential, and ecosystem expansion impact. The most valuable partnerships create network effects that competitors can't easily replicate.
Industry Event Intelligence: Extracting Value from Cybersecurity Conferences
Cybersecurity conferences like RSA, Black Hat, and SANS Cyber Threat Intelligence Summit offer rich competitive intelligence opportunities beyond networking. Tracking competitor participation can reveal strategic priorities and emerging trends. For instance, knowing which events competitors prioritize and what they present on provides insights into their market focus.
Consider this real-world example from RivalSense: HUMAN participated in the IAB Tech Lab Advanced TV Event 2025 in NYC, with Lindsay Kaye, Vice President of Threat Intelligence at HUMAN, and Per Bjorke, Director of Product Management at Google, speaking on BADBOX 2.0 fraud in the CTV/device supply chain. This insight is valuable because event participation highlights a competitor's thought leadership areas and potential collaboration with industry giants, signaling where they are investing resources and seeking influence.
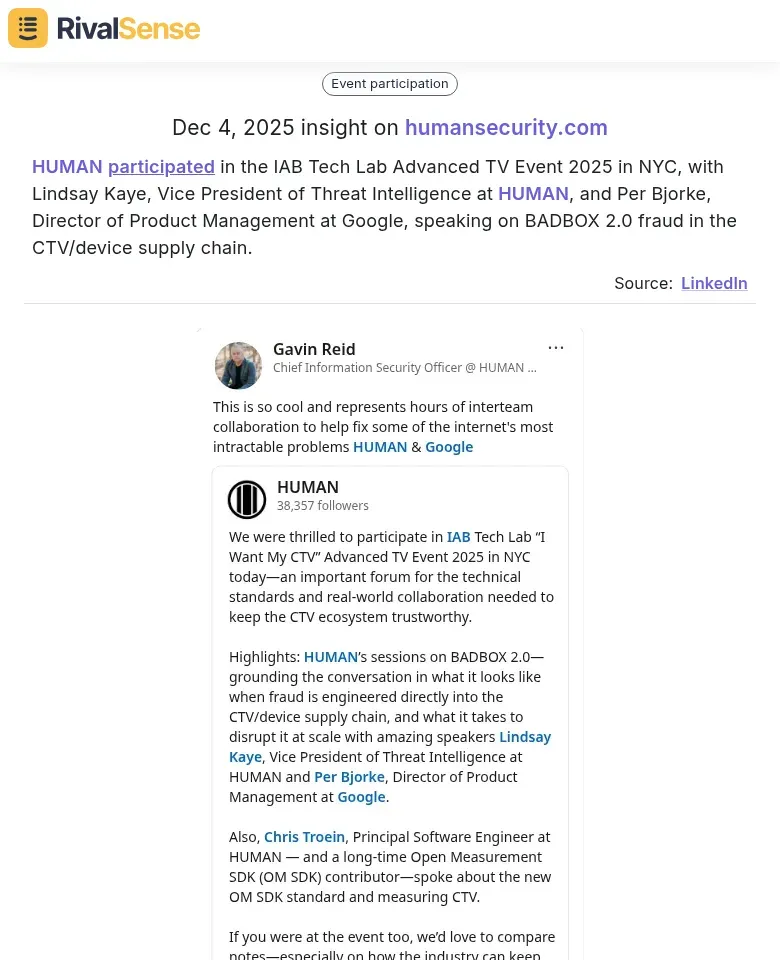
Practical Steps for Conference Intelligence:
- Create a tracking spreadsheet with columns for: conference name, competitor, speaker role, presentation topic, key themes, and partnership announcements
- Analyze participation patterns—are competitors focusing on enterprise vs. SMB events? Are they sponsoring or just attending?
- Monitor shared platforms where competitors co-present—this reveals potential collaboration opportunities or emerging industry alliances
Checklist for Actionable Insights:
✅ Identify which competitors dominate specific threat verticals (cloud security, compliance, etc.)
✅ Track executive movement between speaking slots to gauge market positioning shifts
✅ Note partnership announcements during panel discussions
✅ Document new solution terminology and positioning language
✅ Record audience engagement levels and Q&A focus areas
Pro Tip: Use tools like RivalSense to automate tracking of competitor event participation across multiple conferences. Set alerts for when competitors secure speaking slots at major events—this early intelligence helps you adjust your own conference strategy and identify gaps in your market positioning.
Collaboration Opportunities: When competitors share stages at events like ISACA conferences or co-host workshops, analyze the partnership dynamics. These shared platforms often signal emerging industry standards or collaborative solution development that you could potentially join or counter with alternative alliances.
Technology Integration Insights: Monitoring Solution Deployments
Tracking cybersecurity solution deployments reveals critical competitive intelligence about market expansion and technology adoption patterns. By monitoring how competitors integrate their solutions, you can anticipate market shifts and identify gaps in your own offerings.
Here’s how to monitor these strategic indicators:
1. Track Subsidiary Partnerships for Market Expansion:
- Monitor M&A announcements and strategic partnerships in cybersecurity press releases
- Set up alerts for new regional offices, subsidiaries, or local partnerships
- Analyze partnership announcements with industry-specific players (e.g., banking, healthcare, retail)
- Practical tip: Create a tracking matrix with columns for competitor name, partnership type, geographic region, and target industry
For example, RivalSense captured Brightcom Group's subsidiary OMS partnering with HUMAN to combat digital ad fraud using HUMAN's fraud detection technology. This insight is valuable because it shows how competitors use subsidiary partnerships to enter new markets or enhance their technology stack, giving you clues about expansion strategies and potential competitive threats.
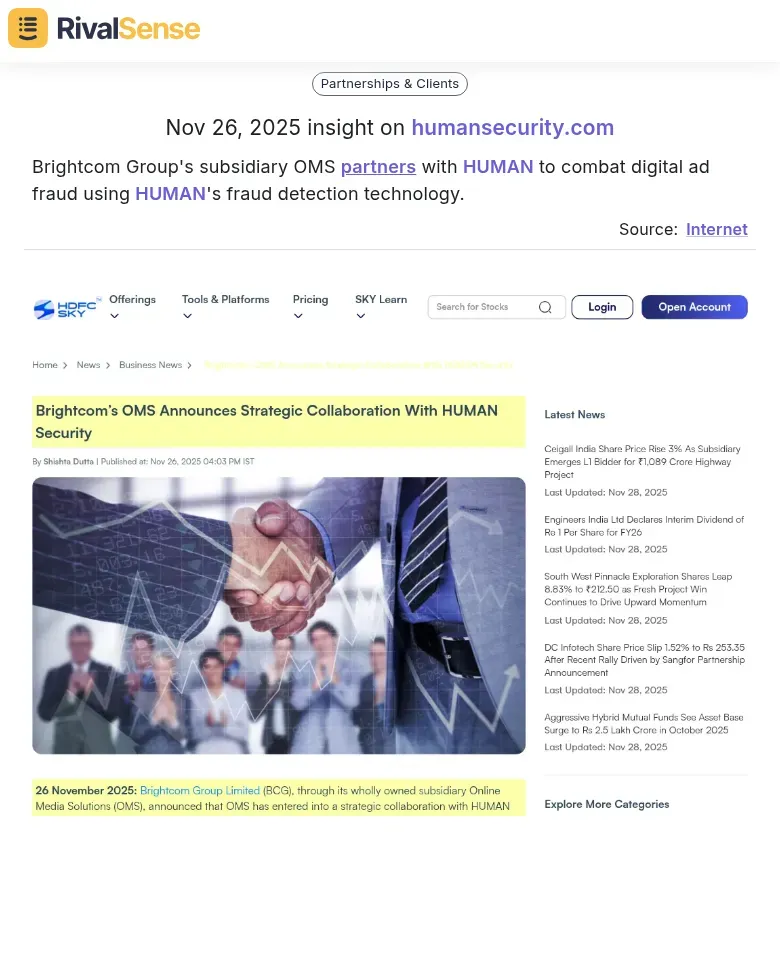
2. Monitor Fraud Detection Technology Adoption:
- Track which competitors are deploying AI/ML fraud detection across different verticals
- Monitor case studies and customer success stories by industry (banking leads, followed by e-commerce, insurance, healthcare)
- Watch for industry-specific solution announcements (e.g., "fraud detection for fintech" vs. "healthcare claims fraud")
- Checklist: Banking/Finance, E-commerce, Insurance, Healthcare, Government, Telecommunications
3. Identify Integration Patterns for Scalability Insights:
- Monitor API integration announcements and developer portal updates
- Track which competitors offer pre-built integrations with major platforms (Salesforce, AWS, Azure, ServiceNow)
- Analyze integration patterns: point-to-point vs. middleware vs. event-driven architectures
- Key indicator: Solutions with extensive API libraries and pre-built connectors demonstrate scalability and market acceptance
- Practical step: Create a scorecard tracking integration breadth (number of connectors), depth (API functionality), and industry-specific adaptations
Pro Tip: Use competitive intelligence tools to automate monitoring of press releases, job postings (especially integration engineer roles), and developer community activity to spot emerging integration patterns before they become mainstream.
Implementation Framework: Building Your Competitive Intelligence Program
Building an effective competitive intelligence program requires a systematic implementation framework. Start by selecting key account tracking software that aligns with cybersecurity-specific needs—prioritize platforms with real-time threat intelligence integration, compliance monitoring capabilities, and API access for seamless connection to your security stack. Evaluate solutions based on source coverage (80+ sources ideal), data freshness, and integration with tools like SIEM systems and threat intelligence platforms.
Establish measurable ROI metrics: track win/loss rates against monitored competitors, time-to-detection improvements for competitive threats, and product roadmap acceleration based on competitor feature analysis. Create a dashboard with KPIs like competitive threat detection rate, intelligence-to-action conversion time, and market share impact from intelligence-driven decisions.
Develop actionable workflows: implement weekly intelligence review meetings with security and product teams, create alert thresholds for urgent competitor moves (major security acquisitions, critical vulnerability disclosures), and establish response protocols. Use a three-tier system: immediate alerts for critical developments, weekly summaries for strategic planning, and quarterly deep-dives for market positioning analysis. Integrate intelligence directly into product development cycles and business development pipelines to ensure competitive insights inform both technical and commercial strategies.
Take Your Competitive Intelligence to the Next Level
To effectively implement the strategies discussed, consider leveraging specialized tools like RivalSense. RivalSense tracks competitor product launches/updates, pricing updates, event participations, partnerships, regulatory aspects, management changes, and media mentions across company websites, social media, the internet, and various registries, delivering all in a weekly email report.
Try out RivalSense for free at https://rivalsense.co/ to assist with the challenges described in this post. Get your first competitor report today and start transforming raw data into actionable strategic insights.
📚 Read more
👉 Data-Driven Competitor Product Insights: Track for Strategic Sales Wins
👉 Real-World Competitor Analysis: Insights and Actionable Strategies
👉 The Strategic Benefits of Real-Time Competitor Alerts: A Practical Guide for Business Leaders
👉 Commercial Laundry Services: Key Account Sentiment Tracking Checklist
👉 How Perplexity's iPad Move Prompted Rivals to Accelerate Mobile Strategy
