Actionable Strategies to Outshine Competitors in Cybersecurity Brand Perception
In cybersecurity, brand perception is how customers view your company's security capabilities, reliability, and trustworthiness. It directly impacts customer trust—studies show 81% of consumers need to trust a brand before buying, and 70% pay more for trusted businesses. Trust and reliability form the foundation: customers must believe their data is safe with you, which differentiates you in a competitive market. Strong brand perception enhances competitive positioning by signaling maturity and future-readiness, attracting enterprise deals and premium pricing.
Practical steps to build cybersecurity brand perception:
✅ Define a clear Unique Value Proposition (USP) that addresses specific security pain points
✅ Communicate brand values like trust and innovation consistently across all channels
✅ Use human-centric visuals and simple language to make security relatable
✅ Publish thought leadership content (blogs, reports) to showcase expertise
✅ Obtain certifications (e.g., ISO 27001, SOC 2) for third-party validation
✅ Train employees to foster a security-first culture, reducing human errors
✅ Monitor competitor branding to identify gaps and opportunities
💡 Tip: Leverage customer success stories and case studies to provide tangible proof of your security effectiveness, building credibility organically.
Leveraging Executive Thought Leadership for Brand Enhancement
Executive thought leadership is your most powerful tool for cybersecurity brand enhancement. Start by securing speaking engagements at top industry events like RSA Conference and Black Hat—these platforms position your leaders as authorities. Prepare 3-5 signature talking points that showcase unique insights on emerging threats like AI-powered attacks.
Tracking competitor executive activities provides valuable intelligence about their market positioning and partnership strategies. For example, this RivalSense insight reveals strategic networking and knowledge-sharing opportunities:
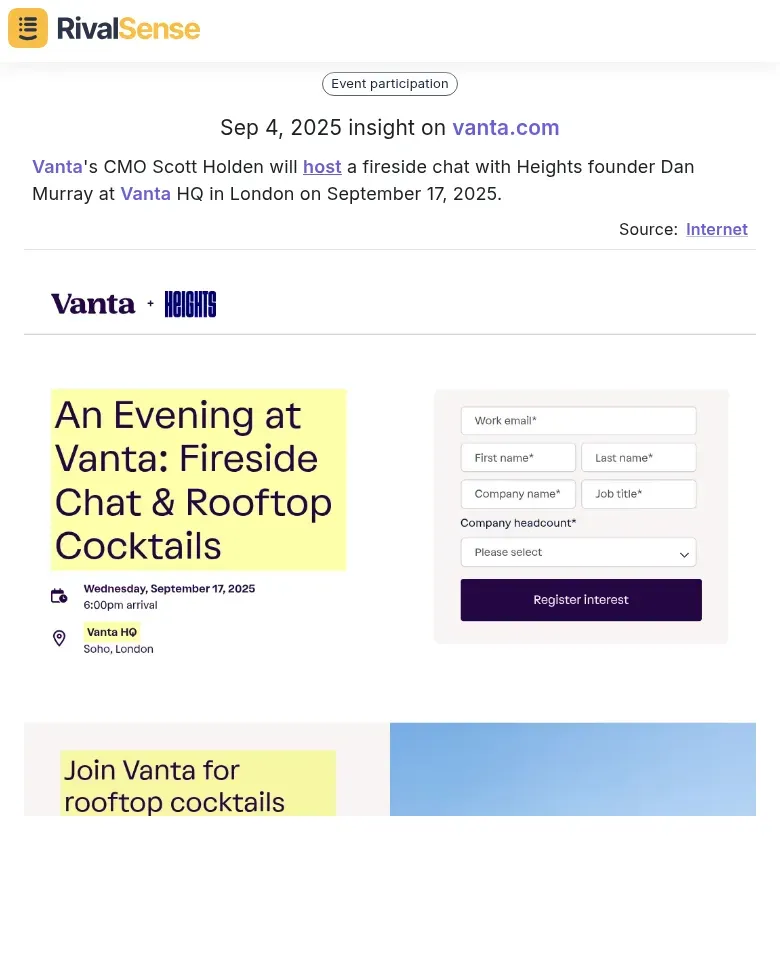
Vanta's CMO Scott Holden will host a fireside chat with Heights founder Dan Murray at Vanta HQ in London on September 17, 2025.
This type of insight helps you understand how competitors are building industry relationships and thought leadership presence, allowing you to identify potential partnership opportunities or speaking engagements for your own executives.
Checklist for executive thought leadership:
- [ ] Identify 2-3 target conferences quarterly
- [ ] Create CEO messaging framework for innovation announcements
- [ ] Establish partnership criteria focusing on shared customer values
- [ ] Measure impact through share of voice in cybersecurity media
Product Innovation as a Competitive Differentiator
Product innovation is your most powerful weapon for cybersecurity differentiation. Launch features that directly solve customer pain points—like AI-powered compliance automation that reduces manual work by 80% or simplified policy management that cuts configuration time in half.
Monitoring competitor product launches helps you understand their innovation priorities and market positioning. Consider this RivalSense insight showing how Vanta addresses customer pain points:
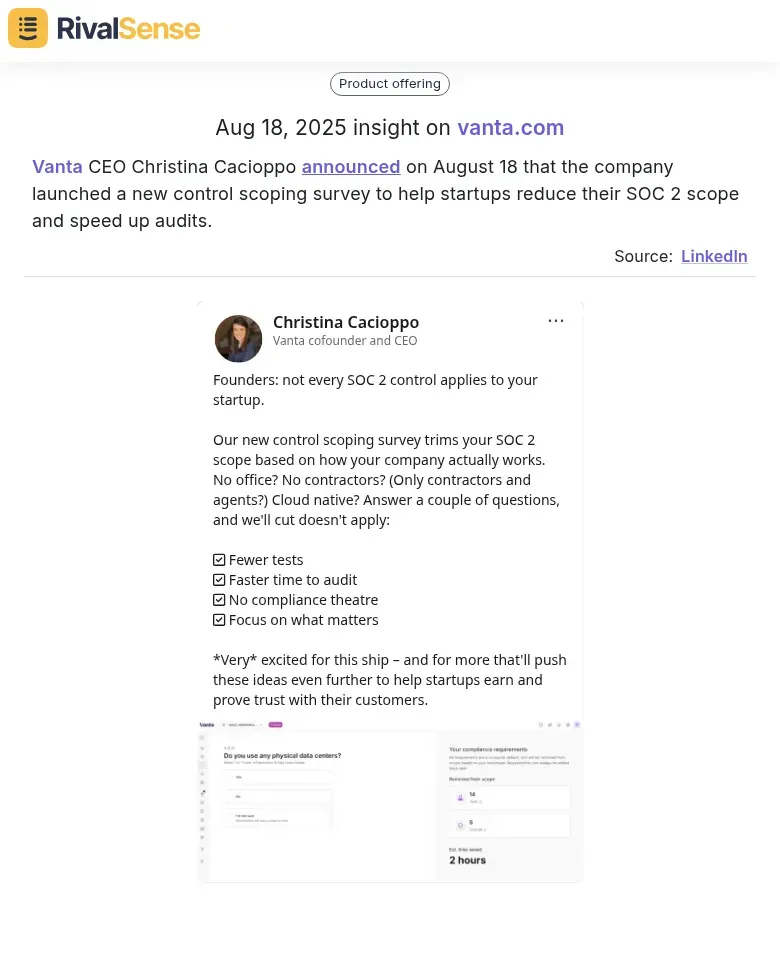
Vanta CEO Christina Cacioppo announced on August 18 that the company launched a new control scoping survey to help startups reduce their SOC 2 scope and speed up audits.
Tracking such product updates helps you benchmark your innovation pace and identify unmet customer needs in the market.
Practical steps for product innovation:
- Conduct quarterly customer interviews to identify top 3 compliance pain points
- Develop features that automate complex regulatory requirements (GDPR, HIPAA, etc.)
- Use product announcements to showcase continuous improvement—highlight how new features reduce complexity
- Position innovations as "compliance simplification tools" rather than technical features
- Create demo videos showing before/after scenarios of reduced administrative burden
💡 Example: Palo Alto Networks' AI Copilots reduced documentation search time by 24x, positioning them as simplicity leaders. Focus on outcomes: "Our automated compliance reporting saves 15 hours weekly" resonates more than technical specs.
Strategic Talent Acquisition and Team Building
In cybersecurity, your team's expertise directly impacts brand perception. With a record 4.8 million professional gap globally, strategic hiring becomes a competitive advantage.
Tracking competitor hiring patterns reveals their strategic direction and technical focus areas. This RivalSense insight demonstrates how talent moves can signal market priorities:
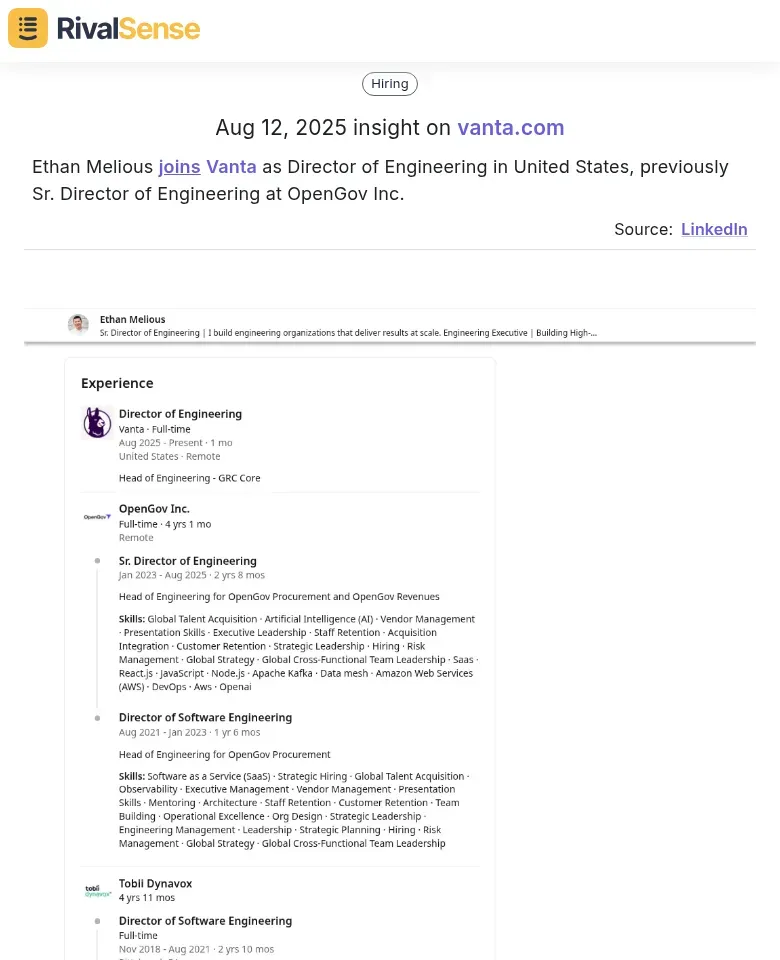
Ethan Melious joins Vanta as Director of Engineering in United States, previously Sr. Director of Engineering at OpenGov Inc.
Such hiring intelligence helps you understand where competitors are investing resources and what technical capabilities they're strengthening, allowing you to adjust your own talent strategy accordingly.
Actionable Steps:
✅ Target Industry Veterans: Prioritize candidates with 5+ years in specialized domains (AI security, cloud infrastructure, Zero Trust)
✅ Leverage Backgrounds Strategically: When hiring experts from regulated industries, highlight their compliance expertise in announcements
✅ Amplify Hiring Wins: Issue press releases for key hires emphasizing specific threat expertise and previous employer prestige
Checklist for Effective Team Building Communications:
- [ ] Include specific technical achievements in hire announcements
- [ ] Connect new expertise to current market threats
- [ ] Feature team expansion in quarterly growth reports
- [ ] Use hires to validate entry into new market segments
💡 Pro Tip: Coordinate hiring announcements with product launches or threat intelligence reports. This positions new talent as enhancing existing capabilities rather than filling gaps.
Content and Community Engagement Strategies
Transform your cybersecurity brand into an authoritative voice through strategic content and community engagement. Start by developing educational content that establishes thought leadership—publish quarterly threat intelligence reports, host expert webinars on emerging threats, and create technical whitepapers with actionable insights.
Use storytelling techniques like human-centric narratives and real-world case studies to make complex concepts accessible; for example, frame ransomware attacks as digital hostage situations with clear victim-impact stories.
Build engagement through community events: launch monthly virtual roundtables where security professionals share best practices, create a private Slack/Discord community for real-time discussions, and host annual cybersecurity challenges or hackathons.
Implementation checklist:
- [ ] Identify 3 key technical concepts to simplify monthly
- [ ] Develop 2 customer success stories quarterly
- [ ] Host at least one interactive webinar per month
- [ ] Create downloadable templates for common security frameworks
💡 Practical tip: Use the "before-after-bridge" framework for case studies—show the security challenge, your solution's implementation, and the measurable outcomes. This approach makes technical achievements relatable while demonstrating tangible value to potential clients.
Measuring and Optimizing Brand Perception Impact
To effectively measure and optimize brand perception impact in cybersecurity, implement a systematic approach. First, track key metrics against competitors using tools for social sentiment analysis, competitive benchmarking, and cybersecurity-specific threat monitoring. Monitor sentiment scores, share of voice, brand mentions, and security incident response times.
Analyze how brand initiatives translate into market advantages by correlating marketing campaigns with sentiment shifts and market share changes. Use A/B testing to measure the impact of different messaging strategies on customer perception.
Continuous refinement strategy:
- Set up automated alerts for brand mentions and sentiment changes
- Conduct quarterly competitive intelligence audits
- Gather direct customer feedback through surveys and interviews
- Monitor dark web chatter for potential reputation threats
- Adjust messaging based on real-time market responses
Practical measurement checklist:
- [ ] Weekly sentiment tracking reports
- [ ] Monthly competitive positioning analysis
- [ ] Quarterly brand perception surveys
- [ ] Real-time alert system for reputation threats
- [ ] Regular strategy review sessions based on intelligence data
Put These Strategies into Action with RivalSense
Implementing these cybersecurity brand perception strategies requires continuous competitor monitoring and market intelligence. RivalSense tracks competitor product launches, pricing updates, event participations, partnerships, regulatory changes, management moves, and media mentions across multiple sources—delivering actionable insights in a weekly email report.
Ready to outshine your competitors? Try RivalSense for free at https://rivalsense.co/ and get your first competitor report today to start transforming your cybersecurity brand perception.
📚 Read more
👉 How to Track Competitor Employee Changes for Strategic Advantage
👉 How Vanta's AI GTM Strategy Reveals Critical Competitor Insights
👉 Unlocking Competitor Social Media Advantages: A Strategic Guide for Business Leaders
👉 How Early Detection of Mapon's Route Planning Expansion Saved 15% Market Share
